To check if any relational database matches the given structure, make sure the data is correct, the design is accurate, all functions work properly, the system runs efficiently, and the database is secure. This can be further divided into the below-mentioned forms:
- Structural Testing: Validate the database schema against the expected structure.
- Data Integrity Testing: Ensure relationships between tables are correctly implemented.
- Functional Testing: Verify if database operations (Create, Read, Update, Delete) perform as expected.
- Performance Testing: Assess query performance and response times.
- Security Testing: Check who can access the database, what permissions they have, and if there are any security weaknesses
Testing Strategy-
1. Structural Testing
- Compare the actual database schema with the expected schema for consistency.
- Verify that all tables, columns, data types, and constraints match the provided model.
- Ensure that primary keys, foreign keys, and unique constraints exist where defined.
- Check for missing or extra fields in the actual database.
Example:
- Scenario: Verify the “Users” table structure.
- Test: Check if the “Users” table exists and has a column named “email” of type VARCHAR(255).
- Expected Result: The table exists, and the “email” column is present with the correct data type and length.
2. Data Integrity Testing
- Make sure that foreign keys correctly point to primary keys.
- Check that there are no records without matching data in related tables.
- Look for duplicate entries in tables that should only have unique records.
- Ensure that necessary fields have values and aren’t left empty when they shouldn’t be.
Example:
- Scenario: Verify that a customer’s address is correctly updated in the database.
- Test: Update a customer’s address and then retrieve the updated record to ensure the address matches the input.
3. Functional Testing
- Test CRUD operations to confirm data is inserted, updated, retrieved, and deleted correctly.
- Check if stored procedures, triggers, and automatic actions in the database work correctly.
- See how the database handles errors and undoes actions when needed.
- Make sure that calculated fields and derived data are created correctly.
Example:
- Scenario: Verify that a user can successfully create a new account.
- Test:
- Navigate to the “Create Account” page.
- Fill in the required fields (username, email, and password).
- Click the “Submit” button.
- Expected Result:
- The user should be redirected to a “Success” page or logged in automatically.
- The new account should be created in the database.
4. Performance Testing
- Check how long queries take to run and find any slow spots.
- Test how the database performs when multiple transactions happen at the same time.
- Test the database with large amounts of data to make sure it can handle growth.
Example:
- Scenario: Measure the time it takes to retrieve 1,000 customer records from the database.
- Test:
- Execute a query to retrieve 1,000 customer records.
- Expected Result:
- The query should complete in less than 1 second.
- Additional Considerations:
- Test with different query types (e.g., SELECT, INSERT, UPDATE, DELETE).
- Test with different data volumes.
- Test with different network conditions.
- Test with different hardware configurations.
5. Security Testing
- Make sure user roles and permissions are set correctly to limit access where needed.
- Check that sensitive data is encrypted or hidden according to rules.
- Test the system that logs and tracks database activities to ensure it’s working.
Plans:
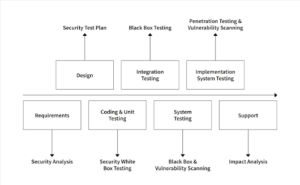
Some examples:
- Valid Login: Test with valid credentials to ensure successful login and access to authorized areas.
- Access Control: Verify that users are only able to access resources they are authorized to access.
- SQL Injection: Test for vulnerabilities by trying to inject SQL code into input fields.
- Cross-Site Scripting (XSS): Test for XSS vulnerabilities by injecting malicious scripts into input fields.
- So on……
Overview structure:
| Test Type | Methodology | Expected |
|---|---|---|
| Schema Validation | Compare the actual schema with the model | No mismatches found |
| Data Integrity | Check foreign key relationships, unique constraint | No data inconsistencies |
| Functional Testing | Performing CRUD operations and validating stored procedures | All transactions execute correctly |
| Performance Testing | Evaluate the performance | Acceptable response time under load |
| Security Testing | Test access control and attempt security breaches | No unauthorized access detected |




