A threat is a potential cause of an incident that can cause harm to a system or an organization while a vulnerability can be defined as a weakness in the system which is exploited by a threat. A threat agent exploits one or more vulnerabilities to carry out a threat. They are discussed in detail below:
Denial of Service:
Denial of Service (DoS) is an attack that is meant to shut down a network or a machine, thereby, making it inaccessible to the users who are intended to use it. DoS attacks flood the target server with traffic, or by sending information that triggers a crash on the server’s end. Victims of DoS generally include web servers of high-profile organizations such as banking, media companies, trade, or government organizations. DoS attacks may not result in the theft or loss of any information but they can cost the victim a great wastage of time and money to get things fixed.
Distributed Denial of Service:
Distributed Denial of Service (DDoS) is a malicious attempt to disrupt the normal traffic of a target network, server, or service by flooding the target or its surrounding infrastructure with Internet traffic. The attacker takes control of several victim systems known as zombies, also known as a botnet by spreading various types of malware. Now, the attacker can shut down a network service by commanding the botnet to send fake traffic that fabricates data.
Securing data in the cloud is the single largest security concern that most organizations have with cloud computing. In any WAN traffic, one must assume that any data can be modified or intercepted. That’s why traffic to and from a cloud service provider is encrypted. Some key mechanisms for protecting data are Access control, Auditing, Authentication, Authorization
Every service model should have mechanisms operating in all these four areas that are based on the security requirements, whether operating through its own local infrastructure or any cloud service provider.
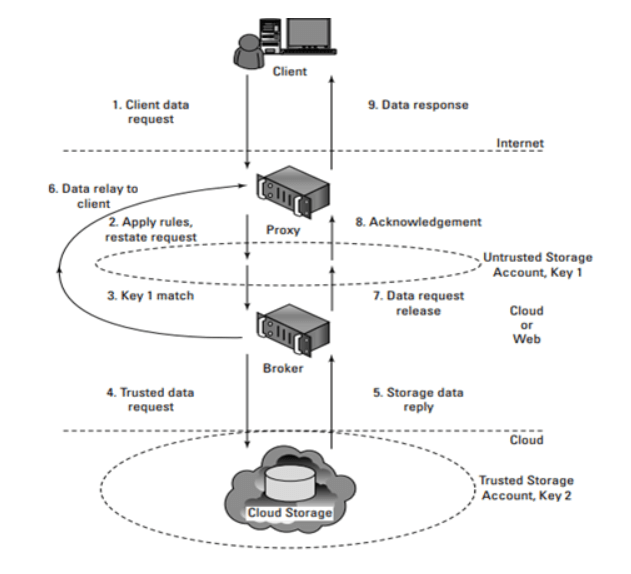
Brokered cloud storage access:
The problem with the data stored in the cloud is that the server can be located anywhere in the cloud service provider’s system which can be in another data center, another country, or in many cases even in another continent. In client/server or with other types of system architectures, one can count on a firewall to serve as the network’s security perimeter but cloud computing has no physical system that can be used to serve this purpose.
When a client makes a request for data, the request goes to the endpoint or external service interface of the proxy, which has only a partial trust.
- The proxy forwards the request to the broker using its internal interface.
- The broker then requests data from the cloud storage system.
- The storage system returns the results to the broker.
- The broker returns the results to the proxy.
- The proxy completes the response by sending the data requested to the client.
-
Encryption:
The data, by default, is coded in a readable form known as plaintext. When transmitted over a network, the risk is unauthorized and potentially dangerous access.
Encryption technology relies on a standard algorithm called cipher to convert original text data into encrypted data, called ciphertext. Access to ciphertext does not disclose the exact details of writing, with the exception of other metadata types, such as message length and creation date. When encryption is used for listening data, data is paired with a string of characters called an encryption key. The encryption key is used to encrypt ciphertext back to its original writing format.
Asymmetric Encryption
A malicious service provider cannot retrieve data from encrypted messages. Refund attempt may also reveal to the cloud service customer -
Hashing:
Hashing is the conversion of a string of characters into a limited number of short lengths or a key that reflects the original string. Hashing is used to identify and retrieve items from the database because it is faster to find an object using the shorter hashed key than to find it using the original value. It is also used in many encryption algorithms.
There are many well-known hash functions used in cryptography. These include message-digest hash works MD2, MD4, and MD5, which is used to incorporate digital signatures into a short form called message-digest, and the Secure Hash Algorithm (SHA), a standard algorithm, which makes it large (60- bit) digestion message and similar to MD4. An effective hash function for storing and retrieving, however, may not work for cryptographic detection purposes or errors.Malware hashes are used by anti-virus programs to identify viruses. They contain the numerical values of the code that differs from this virus. Anti-virus software compares malware hashes and software-hardware hashes within a computer program to detect malware.
The diagram shows the creation of a malware hash by creating a cryptographic hash of malware code to create a path that can be used by anti-virus software to identify the virus. The authors of Malware have learned to customize viruses on each infected machine, creating unique hashes for each copy submitted challenging the anti-virus programs.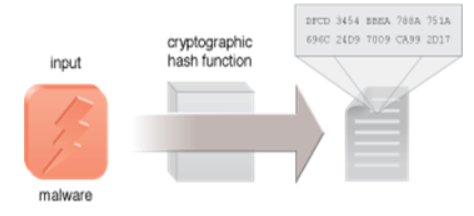
-
Digital Signatures:
The digital signature mechanism is a means of providing data integrity, data authenticity through authentication, and non-repudiation. A message is assigned a digital signature prior to transmission, and if the message experiences any subsequent, unauthorized modifications then it is rendered as invalid. A digital signature provides evidence that the message received is the same as the original message sent by the rightful sender.
Both hashing and asymmetrical encryption are involved in the creation of a digital signature, which exists as a message digest that was encrypted by a private key and appended to the original message. To decrypt the digital signature’s encrypted hash, the recipient verifies the signature validity by using the corresponding public key, which produces the message digest. To produce the message digest hashing mechanism is applied to the original message. Identical results from the two different processes is an indication that the message maintained its integrity.
-
Single Sign-On:
The single sign-on (SSO) mechanism enables one cloud service consumer to be authenticated by a security broker, which establishes a security context while the cloud service consumer accesses cloud-based IT resources. Otherwise, with every subsequent request, the service consumer would need to re-authenticate itself.
The advantage to the SSO machine is how it enables independent IT resources to generate and distribute operational authorization and validation signals. The information originally provided by the cloud client remains active during the user’s session, while its security information is shared with other IT resources. SSO Security Vendor assists when a cloud buyer needs access to cloud-based cloud services. -
Public Key Infrastructure:
A common approach for managing the issuance of asymmetric keys is based on the PKI (public key infrastructure) mechanism, which exists as a system of protocols, practices, rules, and data formats that enable large-scale systems to securely use public-key cryptography. This system is used to associate public keys with their corresponding key owners (known as public-key identification) while enabling the verification of key validity. PKIs have digitally signed data structures that rely on the use of digital certificates, that bind public keys to certificate owner identities, as well as to related information, such as validity periods. A third-party certificate authority (CA) digitally signs the Digital certificates.
The components of a PKI include a CA that issues the certificates, a registration authority (RA) to approve the issuance of the certificates, a public directory containing the issued certificates, and the certificate revocation list (CRL).
-
Identity and Access Management:
Cloud Identity and Access Management typically include the following features:
Single Access Control Interface: Cloud IAM solutions provide a clean and consistent access control interface for all cloud platform services. All cloud services can use the same interface.
Enhanced Security: You can define increased security for critical applications.
Resource-level Access Control. You can define roles and grant permissions to users for allowing them to access resources at different granularity levels.
StudySection gives an opportunity to beginners and experts in .NET framework to go through StudySection’s .NET Certification Exam and get a .NET certification for enhancement of career in programming. If you have knowledge of the .NET framework then you can get a certificate through an online exam at StudySection.




